The Magnitude of RockYou2024
The RockYou2024 compilation, posted by a forum user named ObamaCare, is an alarming update to the already massive RockYou2021 file. RockYou2021, which contained 8.4 billion plaintext passwords, was previously the largest known password compilation. However, RockYou2024 integrates these older leaks with an additional 1.5 billion new passwords collected between 2021 and 2024, resulting in a 15% increase.
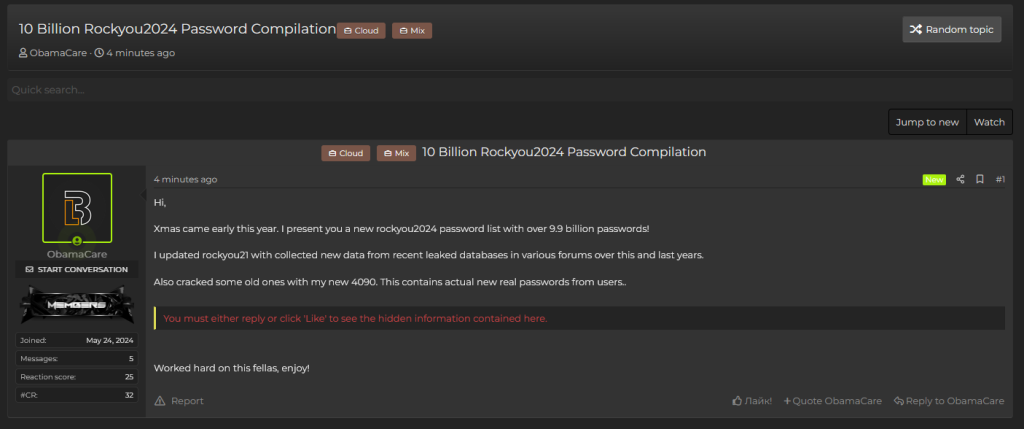
Cybernews researchers have cross-referenced the passwords in RockYou2024 with data from their Leaked Password Checker, revealing that the compilation includes both old and new breaches. This vast collection of real-world passwords poses a severe risk, as it heightens the potential for credential stuffing attacks, where cybercriminals use stolen credentials to gain unauthorized access to user accounts.
The Risks and Consequences
The implications of the RockYou2024 leak are profound. Credential stuffing attacks can lead to widespread data breaches, financial fraud, and identity theft. Such attacks exploit the common practice of password reuse, where individuals use the same password across multiple platforms. This vulnerability allows hackers to gain access to various accounts with ease, causing significant harm to both individuals and businesses.
Recent incidents underscore the severity of credential stuffing attacks. Companies like Santander, Ticketmaster, and Advance Auto Parts have fallen victim to these attacks, resulting in substantial financial and reputational damage. The RockYou2024 compilation, with its nearly 10 billion passwords, provides a rich resource for threat actors to conduct brute-force attacks and compromise a wide array of online services.
Protecting Yourself Against Password Leaks
While the leak itself cannot be undone, there are several steps individuals and organizations can take to protect themselves from the fallout of the RockYou2024 breach:
- Reset Compromised Passwords: Immediately change passwords for all accounts associated with the leaked passwords. Ensure that new passwords are strong, unique, and not reused across different platforms.
- Enable Multi-Factor Authentication (MFA): Wherever possible, enable MFA to add an extra layer of security beyond just a password. This can significantly reduce the risk of unauthorized access.
- Use Password Managers: Password manager software can securely generate and store complex passwords, mitigating the risk of password reuse and simplifying the management of multiple accounts.
- Regularly Check for Compromises: Utilize tools like Cybernews’ Leaked Password Checker or HaveIBeenPwned.com to monitor if your passwords have been exposed in any breaches. Regular checks can prompt timely updates to compromised credentials.
The Evolution of Password Leaks
The RockYou2024 leak is not an isolated incident. It follows a trend of increasingly large password compilations being shared online. Three years ago, the RockYou2021 compilation shocked the cybersecurity world with its 8.4 billion passwords, which was itself an expansion of data breaches dating back to 2009. The latest RockYou iteration likely includes information from over 4,000 databases collected over more than two decades.
Cybernews researchers believe that the sheer size of the RockYou2024 compilation means that any system not protected against brute-force attacks is at risk. This includes everything from online services to internet-facing cameras and industrial hardware. The combination of RockYou2024 with other leaked databases could lead to a cascade of data breaches and identity thefts, further emphasizing the need for robust security measures.
The RockYou2024 leak represents a significant escalation in the ongoing battle between cybersecurity professionals and threat actors. With nearly 10 billion passwords now in the hands of hackers, the importance of strong, unique passwords and multi-factor authentication cannot be overstated. By taking proactive measures and staying informed about potential compromises, individuals and organizations can better protect themselves against the ever-evolving landscape of cyber threats.


